Enable MitID in your services
To enable MitID
please contact support and we will be able to assist in providing access. Nets is a MitID Broker and will help establish access and configure the service according to your need.
General information about MitID:
Timeline
MitID was made available through the E-Ident service in October 2021. The E-Ident service are using the broker delivered by Signaturgruppen. From the beginning of October 2021, all users started to receive their MitID identity.
Information about the end user
The information returned about the end user is listed in the table below. The content may change as the MitID development proceeds.
Authentication Assurance Level
|
aal | AAL | One of https://data.gov.dk/concept/core/nsis/Low https://data.gov.dk/concept/core/nsis/Substantial https://data.gov.dk/concept/core/nsis/High
|
| Authorised to represent |
authorized-
_to_represent Requires scope=organisation |
AUTHORIZED-
_TO_REPRESENT | The organisation number (CVR number) of the organisation the user is authorised to represent. Only available when using the
Private MitID - on behalf of companies function. |
Birth date | birthdate Requires scope=profile |
DOB | The user's date of birth. |
| Danish CPR number | dk_ssn /
ssn Requires scope=ssn |
DK_SSN Requires returnssn=true | The end user's social security number (CPR number). For the OIDC protocol, this is returned in both the
dk_ssn and
ssn claim. |
| Identity Assurance Level |
ial |
IAL | One of https://data.gov.dk/concept/core/nsis/Low https://data.gov.dk/concept/core/nsis/Substantial https://data.gov.dk/concept/core/nsis/High
|
Type of identifyication
| identity_type | IDENTITY_TYPE
| One of: Professional indicates Erhverv user
|
Level of Assurance
| acr
| ACR
|
Accepts acr_values as urn:eident:acrp:level:high or urn:eident:acrp:level:substantial or urn:eident:acrp:level:low Always returns- urn:eident:cert:eidas:high
|
| Level of assurance | loa | LOA | One of https://data.gov.dk/concept/core/nsis/Low https://data.gov.dk/concept/core/nsis/Substantial https://data.gov.dk/concept/core/nsis/High
|
| MitID amr values | mitid_amr | MITID_AMR | Possible values for MitID are:
password
code_token
code_reader
code_app code_app_enchanced u2f_token
Possible values for MitID Erhverv are:
mitid:password
mitid:code_token mitid:code_reader mitid:code_app mitid:code_app_enchanced mitid:u2f_token
|
| MitID UUID | mitid.uuid /
pid |
MITID_UUID | Unique ID for this identity. |
| Name | name Requires scope=profile | FULLNAME | Name of user. |
NemID PID
|
nemid.pid
Requires scope=nemid.pid
|
NEMID_PID
Requires return_nemid_pid=true
| If the user has a NemID identity, this will be the users unique NemID PID value.
|
| Organisation name |
organisation-
_name Requires scope=organisation | ORGANISATION-
_NAME | Name of the organisation the end user is authorised to represent. Only available when using the
Private MitID- on behalf of companies function. |
Organisation number (CVR)
| organisation_number Requires scope=organisation |
ORGANISATION-
_NUMBER | Organisation number of end user. Only available when using the
Private MitID- on behalf of companies function. |
Reference Text
| reference_text
| REFERENCE_TEXT
| Reference text from MitID and/or Erhverv transactions
|
Transaction text
| transaction_text
Requires scope=openid
| NA
| The transaction text used for the
transaction signing feature.
|
SHA256 digets of transaction text
| transaction_text_sha256
Requires scope=openid
| NA
| Base64 encoded SHA256 digest of the MitID transactiontext identity provider parameter.
|
Retrieve SSN (CPR)
The CPR number (Danish social security number) can be retrieved in this way:
When this is set, the user will be prompted for their CPR number and this will be returned in the ID Token (OIDC) and Assertion (SAML). The CPR number will be returned in the
dk_ssn and
ssn claim in the ID Token and as the
DK_SSN attribute in the SAML assertion.
CPR step-up flow
The CPR step-up flow can be used to request the CPR number for already authenticated users. If the CPR number is not already known when the user has authenticated, you can start CPR step-up using the current authentication transaction. The user is then prompted to enter CPR but does not have to re-authenticate. This does not add any additional cost to the transaction.
For OpenID Connect, start CPR step-up by starting an authentication with the parameters
transaction_id and
scope=ssn. For SAML, set
returnssn=true and
transaction_id. This will reuse the previous transaction for the step-up flow.
For OIDC protocol, the
transaction_id parameter value would be
jti claim from ID token.
For SAML protocol, the value for
transaction_id could be found at '/Response/Assertion/@AssertionID' from assertion response. For eg. value of attribute
AssertionID=TI2-617b5cdc6fb84f16a6022e328d970bb7 then transaction_id value would be
617b5cdc6fb84f16a6022e328d970bb7.
It leads to an error response if the CPR step-up flow is requested after the validity of the ID token or SAML assertion. The validity of an ID token and a SAML assertion is 15 minutes.
After the user has inserted the CPR number, you need to request a new ID token or SAML assertion.
Level of assurance and authenticator assurance level
The level of assurance for a specific identification may be set using the
loa_value parameter and the authenticator assurance level may be set using the
aal_value parameter. Both parameters accept these values:
- low
- substantial (default if not set)
- high
If the
loa_value is set, the
aal_value will be ignored. If both the
loa_value and the
aal_value parameter is undefined in the request, the loa_value parameter will as default be set to
substantial.
The actual used values will be returned as loa and aal claims/attributes in the ID Token/SAML assertion. In addition, ial and mitid_amr claims are returned. See the table above for the possible values.
Note: The customer must validate that the returned values are as expected.
Return the user's NemID PID value
During the migration phase, it may be useful to know the MitID user's NemID PID value if the user has previously had a NemID. It is possible to request that during a MitID identification. To get the user's NemID PID value in return you need to:
- For OIDC, add the scope nemid.pid to the identification request. The PID value will be returned in the nemid.pid claim.
- For SAML, add the request parameter return_nemid_pid=true to the identification request. The PID value will be returned in the NEMID_PID attribute.
If the nemid.pid scope or return_nemid_pid parameter is set, the user will be requested to enter his/her CPR number and the ID Token/SAML assertion will include the user's NemID PID value.
User experience
The user may be presented with a choice to log in using MitID as in the first picture below. When the user selects MitID he/she will be redirected to the Nets broker for MitID. For E-Ident customers using the Embedded UI option, the service will break out of iframe when the user is directed to MitID.
Note: The E-Ident service was recently updated with a third UI option - pop-up UI. As the user is redirected to the Nets broker for MitID during the identification, pop-up UI may be an option to consider when adding MitID as an identification method. Read more about the pop-up UI.
EID selection page (optional)
The below page is optional. Users may be sent directly to MitID by using the
amr_values/forcepkivendor parameter on the identification request. The parameter value must be set to
mitid and/or mitid:mitid_erhverv. Read more about the parameters for
OIDC and
SAML. The picture below is an illustration of the page for pop-up and standalone UI modes.
MitID client pages
Step 1 - enter user ID. This page may be skipped using the
presetid/login_hint parameter:
Next steps - this may vary dependent on the level of assurance and user preferences. It may be password, OTP, MitID app actions etc. Here illustrated with entering password:
Enter CPR page
The CPR-page is shown when:
- OIDC: Scope parameter contains SSN and appended to the identification request.
- SAML: returnssn parameter is set to true and appended to the identification request
Customized UI options
The MitID client UI may be customized by using one of four UI templates. The MitID client is in the square while the customer's logo is in the dotted square.
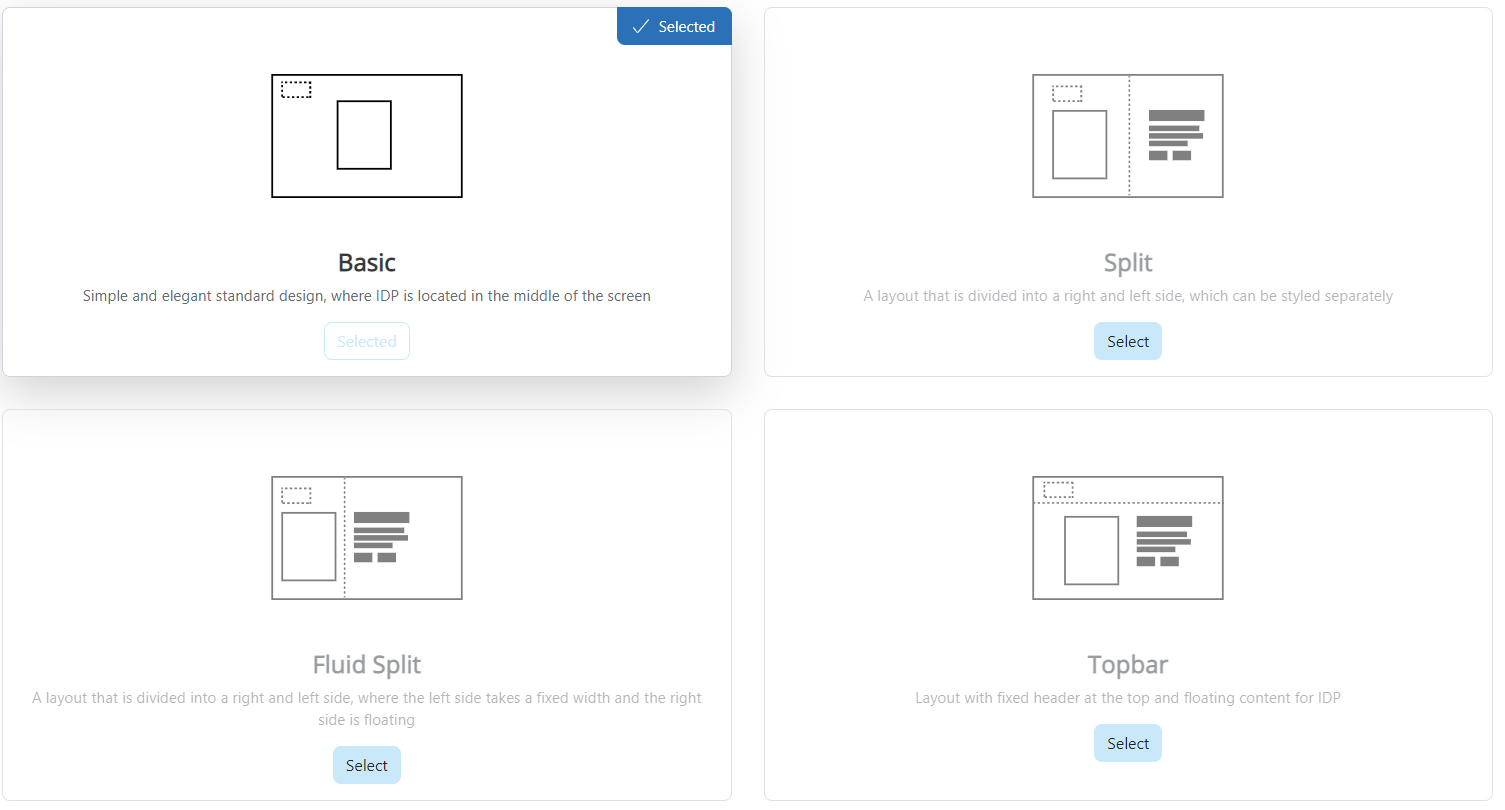 Templates and customization:
Templates and customization:
- Basic: Customers may set the background colour.
- Split, Fluid Split and Topbar: Customers may set two different background colours, text color and supply a welcome text and an optionally CPR page text.
- In all templates, the customer logo may be added. The logo file should be 150 x 37 pixels.
Background colours must be given as hex format (example: #ffffff).
Here is an example of a customized page based on the "Split" template:
Preset ID and Login hint
It is possible to preset the user ID and hence skip the first page in the logon flow. The presetid=<mitid.uuid> / login_hint=<mitid.uuid> parameter must be appended to the identification request and the parameter value must be set to the user's mitid.uuid. If that is set, the user will be directed right to the next page. A general description of the presetid and login_hint parameter is found here.
The presetid/login_hint parameters are not applicable for MitID Erhverv.
Reference text
The user may be shown a reference text throughout the identification. To add a reference text, append the reference_text parameter to the identification request. The reference text will be displayed to user in either the MitID app or, in case MitID app is not used, in the MitID client.
The reference text may be up to 130 characters. A short description of the parameter can be found here:
Transaction text signing
The transaction text signing feature from the Nets eID broker is offered during a MitID identification. During the identification, the user will be presented with the signing text. The text can either be in HTML or text format.
Prerequisite for using the feature:
To use the functionality, two parameters must be appended to the identification request:
-
transactiontext - max length 600 char
-
transactiontext_type -
html or
text
Allowed HTML tags:
- html, body, head, style, title, div, p, ul, li, h1, h2, h3, h4, h5, h6, table, font, tr, th, td, i, u, b, center, a, q, small
Disallowed:
- CSS expressions and embedded script links for style tag.
-
CSS expression attributes.
-
Any on- attributes, such as onload, onclick etc.
-
Script link attributes, such as src, dynsrc, lowsrc, javascript: etc.
The ID token will include these new claims:
- transaction_text
- transaction_text_sha256
- transaction_text_type
The ID token information is also available at the discovery endpoint.
HTML signing
Note: The transaction text signing is not the same as the reference text functionality described above or
the MitID signing functions through E-Signing.
MitID logo and design
MitID design requirements and logos can be downloaded from the Nets eID broker
here.
MitID Erhverv for companies
MitID Erhverv makes it easier for companies to administer user rights, and it is more flexible when business and associations log in to digital self-service solutions, for instance to check their Digital Post, report VAT, etc.
To enable MitID Erhverv you need to explicitly set the
amr_values/forcepkivendor parameter in the identification request. The parameter value must be set to
mitid:mitid_erhverv and may be combined with other IDP selection values. Read more about the parameters for
OIDC and
SAML.
MitID Erhverv flow
Both ID types, Private ID (MitID) and Business ID (Erhverv), can be supported in one single authentication request. After successful authentication, the user can select the applicable ID type.
Note: Business ID also includes identities of type “Private MitID on behalf of companies".
The request parameter "amr_values" will control the selectable ID types.
- Setting amr_values=mitid:mitid_erhverv: Business ID
- Setting amr_values=mitid,mitid:mitid_erhverv: Private ID and Business ID
MitID Erhverv client pages
Step 1 – enter user ID.

Step 2: Next steps may vary dependent on the level of assurance and user preferences. It may be password, OTP, MitID app actions etc. Here illustrated with scanning QR code:

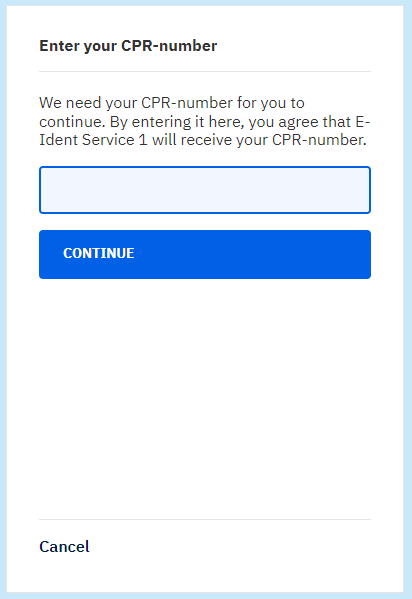
Enter CPR page:
The CPR-page is shown when:
- OIDC: identification request scope parameter contains SSN.
- SAML: identification request returnssn parameter is set to true.
ID Type selection page:
From this page, the user will select the applicable type of identity.
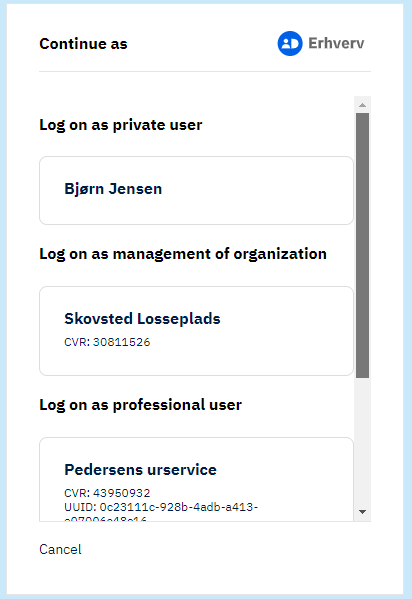
Log on as private user:
This option may be shown if amr_values parameter contains the value “mitid". See more about regular MitID at the top of this page.
Log on as management of organization (Business ID):
This option is shown if the user has a management role in the company.
Log on as professional user (Business ID):
This option is shown if the user has a Business ID from a company.
About Private MitID on behalf of companies
If the user has selected from the management of organization option, the CVR number of the selected organisation will be added to the following claim/attribute:
- OIDC: nemlogin.auth_to_repr claim
- SAML: NEMLOGIN.AUTH_TO_REPR attribute
Test user: Covering all three identity types: Bjørn2712
About CPR
You should only request CPR from the user if you need to retrieve CPR information.
If you require CPR for MitID, but not for Business, you have two options:
Option 1: Always request CPR. This option will force users to have to input their CPR, also for Business login.Option 2: Implement MitID CPR step-up to ensure users only must input CPR when this information is required. See documentation here: https://www.nets.eu/developer/e-ident/eids/Pages/mitid.aspx#mitidcprstepup
Local IDP
As a local identity provider, an organisation can locally issue authenticators to users, which they can use to log into their own systems and in public self-service solutions. Local IDP issuing organisation will have to adhere to regulations and meet requirements of the NSIS standard.
Local IDP is visible as a selection in the MitID Erhverv login screen and will let the user login using this option. You don't need to know anything about Local IDP. It is a native part of MitID Erhverv.
For more information, check out the official MitID Erhverv and Digst pages:
Additional information for MitID Erhverv
Age
| nemlogin.age |
NEMLOGIN.AGE | Age of Erhverv user |
Authorized to represent
| nemlogin.auth_to_rep |
NEMLOGIN.AUTH_TO_REPR | CVR number of the organisation the user is authorised to represent. Only included if the user has selected the management of organisation option. |
Unique ID
| nemlogin.cpr_uuid |
NEMLOGIN.CPR_UUID | Unique ID for Erhverv user |
Company CVR
| nemlogin.cvr |
NEMLOGIN.CVR | Company CVR for Erhverv user
|
Date of birth
| nemlogin.date_of_birth |
NEMLOGIN.DATE_OF_BIRTH | Date of birth for Erhverv user
|
Email address
| nemlogin.email |
NEMLOGIN.EMAIL |
Email address for Erhverv user (may be empty)
|
Family name
| nemlogin.family_name |
NEMLOGIN.FAMILY_NAME | Family name for Erhverv user
|
Given name
| nemlogin.given_name |
NEMLOGIN.GIVEN_NAME | Given name for Erhverv user
|
| Identity Assurance Level |
nemlogin.ial |
NEMLOGIN.IAL |
One of
https://data.gov.dk/concept/core/nsis/Low https://data.gov.dk/concept/core/nsis/Substantial https://data.gov.dk/concept/core/nsis/High
|
Name
|
nemlogin.name |
NEMLOGIN.NAME | Name of user.
|
Role ID
|
nemlogin.nemid.rid
| NEMLOGIN.NEMID.RID
| Employee RID from NemID migration (or assigned)
|
Company name
|
nemlogin.org_name |
NEMLOGIN.ORG_NAME |
|
Company P number
|
nemlogin.p_number |
NEMLOGIN.P_NUMBER |
(may be empty)
|
Professional Unique ID
|
nemlogin.persistent
_professional_id |
NEMLOGIN.PERSISTENT
_PROFESSIONAL_ID | Global UUID/ID from EIA
|
Company SE number
|
nemlogin.se_number
|
NEMLOGIN.SE_NUMBER
| Company SE number for Erhverv user (may be empty)
|